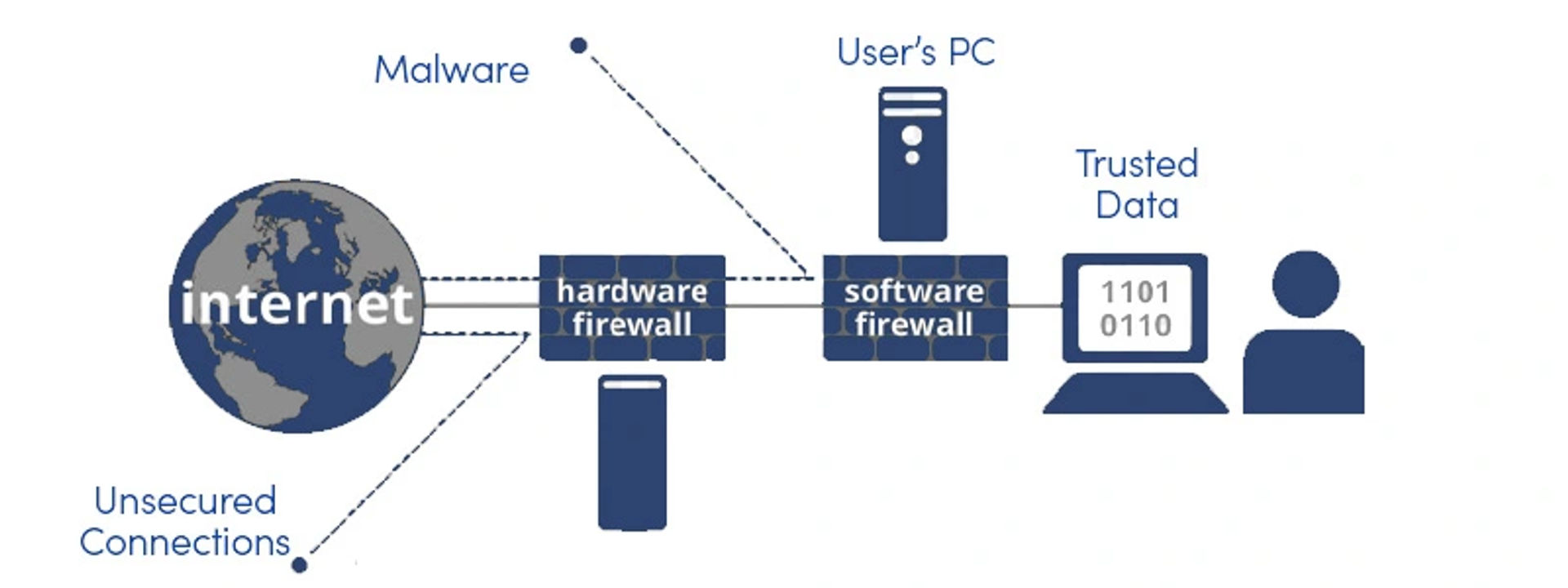
The smooth segue of business from offline to online surely took it to a more productive level. However, working on a platform connected to several known or unknown networks every time is not as safe as it is with private networks. And now, with That's why Network Security is a must. If you're concerned about not having the rightful knowledge, you shouldn't be, as we bring to you a solution, Network Firewall Security.
The authentication of Firewalls can be seen in a research paper, An Overview Of Firewall Technologies, by Habtamu Abie, which claims firewalls are one of the most protective mechanisms. It says “A Firewall protects a network by guarding the points of entry to it. Firewalls are becoming more sophisticated day by day, and more features are being constantly added to them.” We'll discuss and unfold Network Firewall Security in this same context and find out the benefits attached to it so that you understand Network Firewall Security well enough to use or recommend it to someone else.
What Is Network Firewall Security?

Network Firewalls are the security solutions that help protect your networks against unauthorized or unwanted traffic. If you adopt Network Firewall Security, no malware can trespass or try to come in your way. So, in a way, it blocks non-authentic access to private networks and majorly intranet.
Network Firewall Security uses policies that limit or destroy illegal access to your private networks. One plus point of this security device is that it allows only authorized traffic to your networks. Network Firewall Configuration makes sure to verify every data passing through it. To put it simply, Network Firewall Security filters out the data that don't fit the security criteria of Firewalls. In addition to doing all of this, Network Firewall Security uses highly secure authentication certificates and logins to manage remote access.
Network Firewalls Security further bifurcates into Software Firewalls and Hardware Firewalls.
Let's look at them individually.
Software Firewalls
Software Firewalls are installed on computer devices, operating systems, or a network device manufacturer, that provides micro-control over features like network protection. Software Firewalls remain effective when dealing with standard accesses and attempts, but once sophisticated network breaching occurs Software Firewalls are not very useful.
Hardware Firewalls
Hardware Firewalls are a built-in component of any networking device used for corporate purposes. Hardware Firewalls are considered an integral part of the conventional network security and configuration. Hardware Firewalls include at least four ports of networks that smoothly connect your devices to multiple systems.
In addition to these two divisions, Network Firewall Security has several other types that play a significant role in business. We'll further discuss the various types of firewall security.
What Are The Types Of Network Firewall Security?
There are 5 major types of Network Firewall Security, which are:
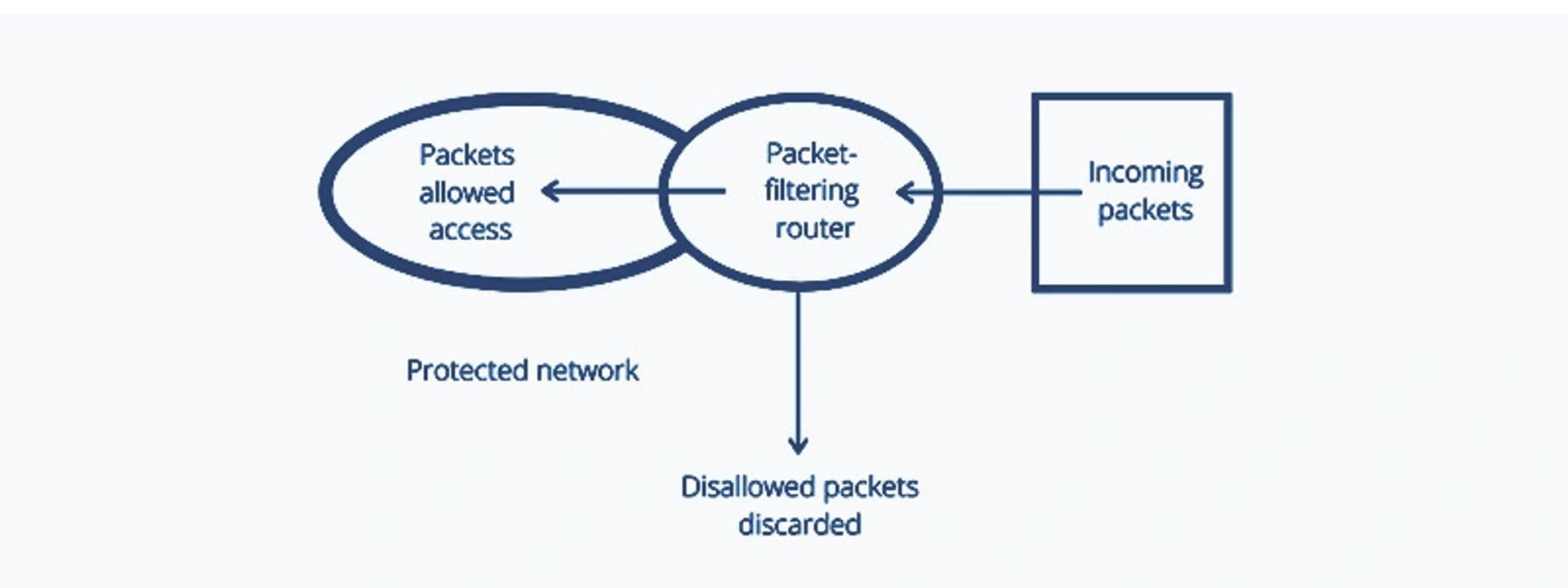
 Packet Filtering Firewall
Packet Filtering Firewall
Packet Filtering Firewall controls the flow of incoming and outgoing network data or traffic. It is a security feature that examines each packet consisting of control information and user data. Packet Filtering Firewall tests these packets per a series of predefined rules. A Packet Filtering Firewall may not be a good fit for every case, however, this cost-effective option is still the best solution for certain situations.
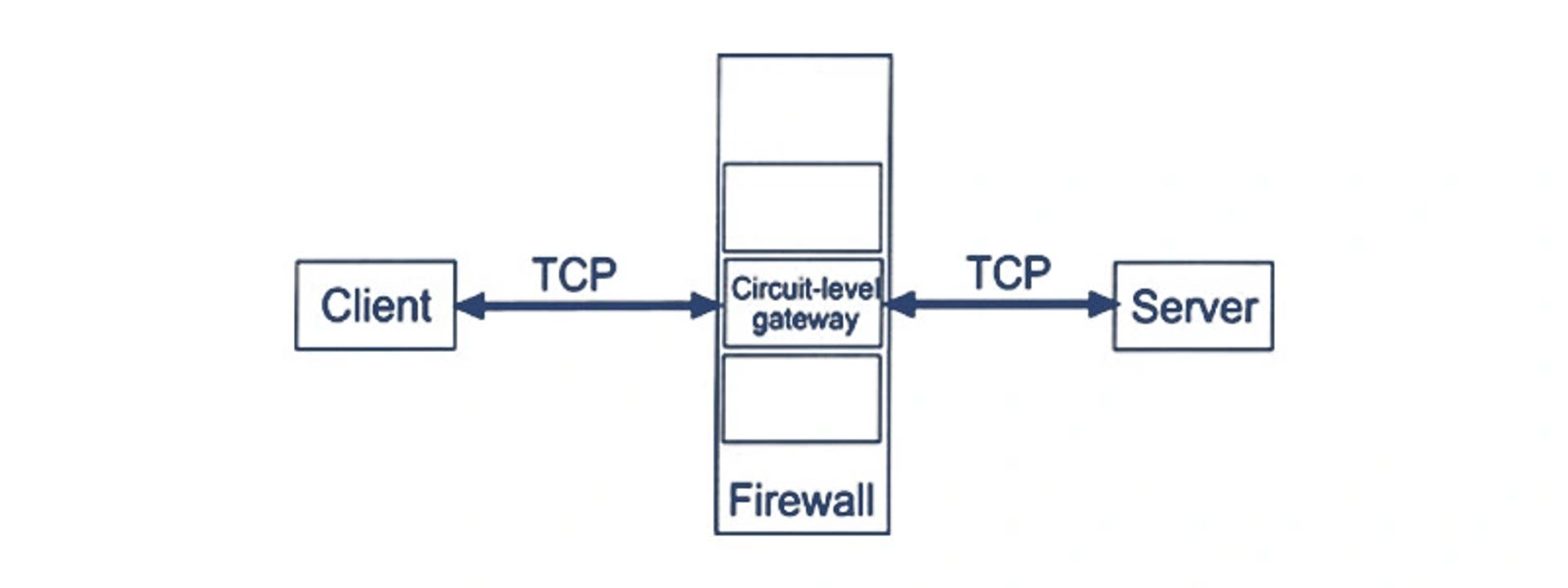
 Circuit-Level Gateway
Circuit-Level Gateway
Circuit-Level Gateway is firewall security that works between Open Systems Interconnections (OSI) and various application layers such as session layers. It is another way to detect malicious activities that provide User Datagram Protocol (UDP) and Transmission Control Protocol (TCP). Circuit-Level Gateways should be used in conjunction with other systems.
With the comeback of the physical inventory scanner function to the QB POS version, CipherLab 8000 and CipherLab 8001 have been added back to the list of POS-compatible scanners. Due to its plug-and-play mechanism, users get improved accessibility and increased usability.
 Application-Level Gateway
Application-Level Gateway
Application-Level Gateway is also known as Application Layer Gateway or Application Layer Proxy. These proxy firewalls function as the only entry and exit point from networks. These firewalls are used to prevent web threats, hence keeping the enterprise data safe.
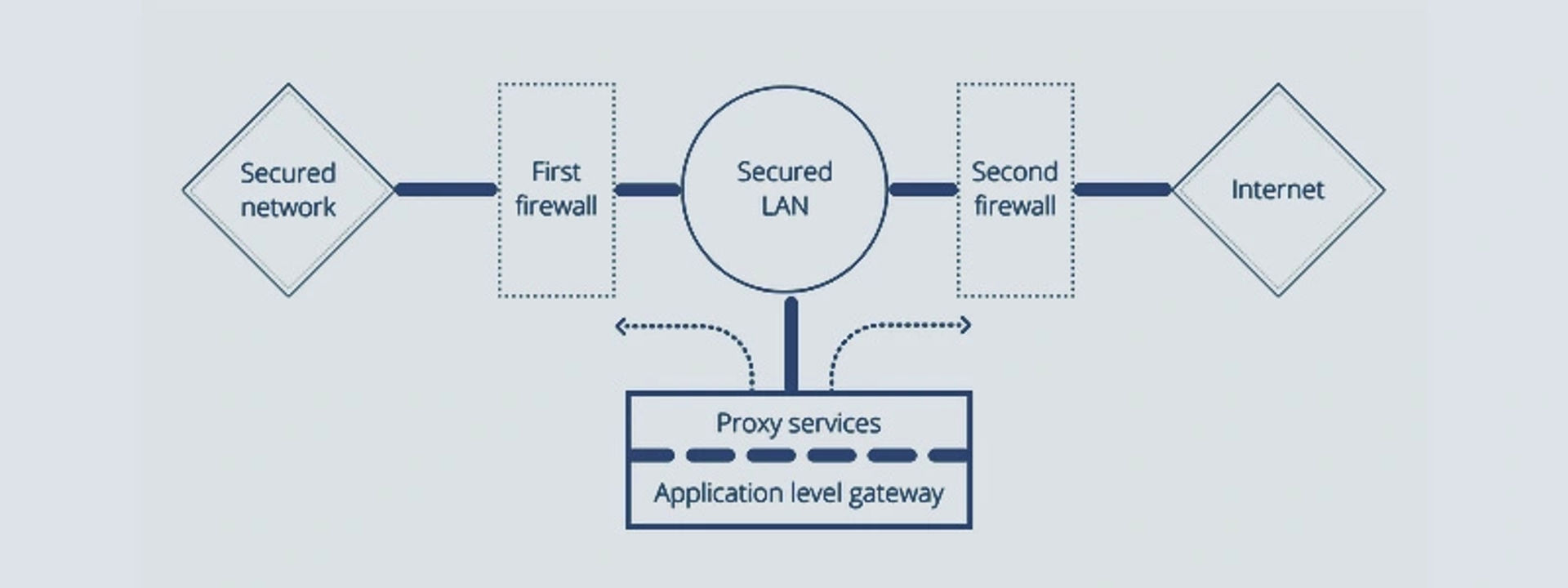
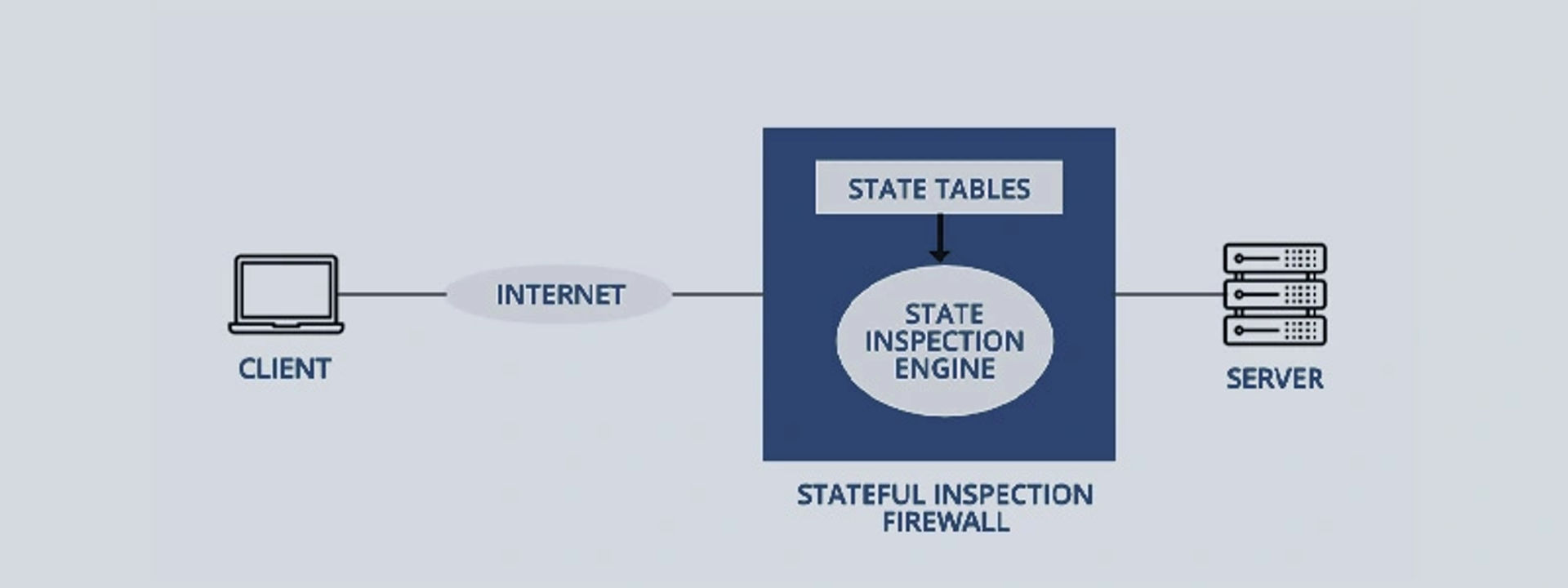
 Stateful Inspection Firewall
Stateful Inspection Firewall
Stateful Inspection Firewall takes care of the traffic between two or more networks. It does not only examine packers but also keeps track of whether the packets are a part of an established TCP (Transport Control Protocol) or some other network. It uses the sources, destination address, IP flags, and port number for keeping track of things.
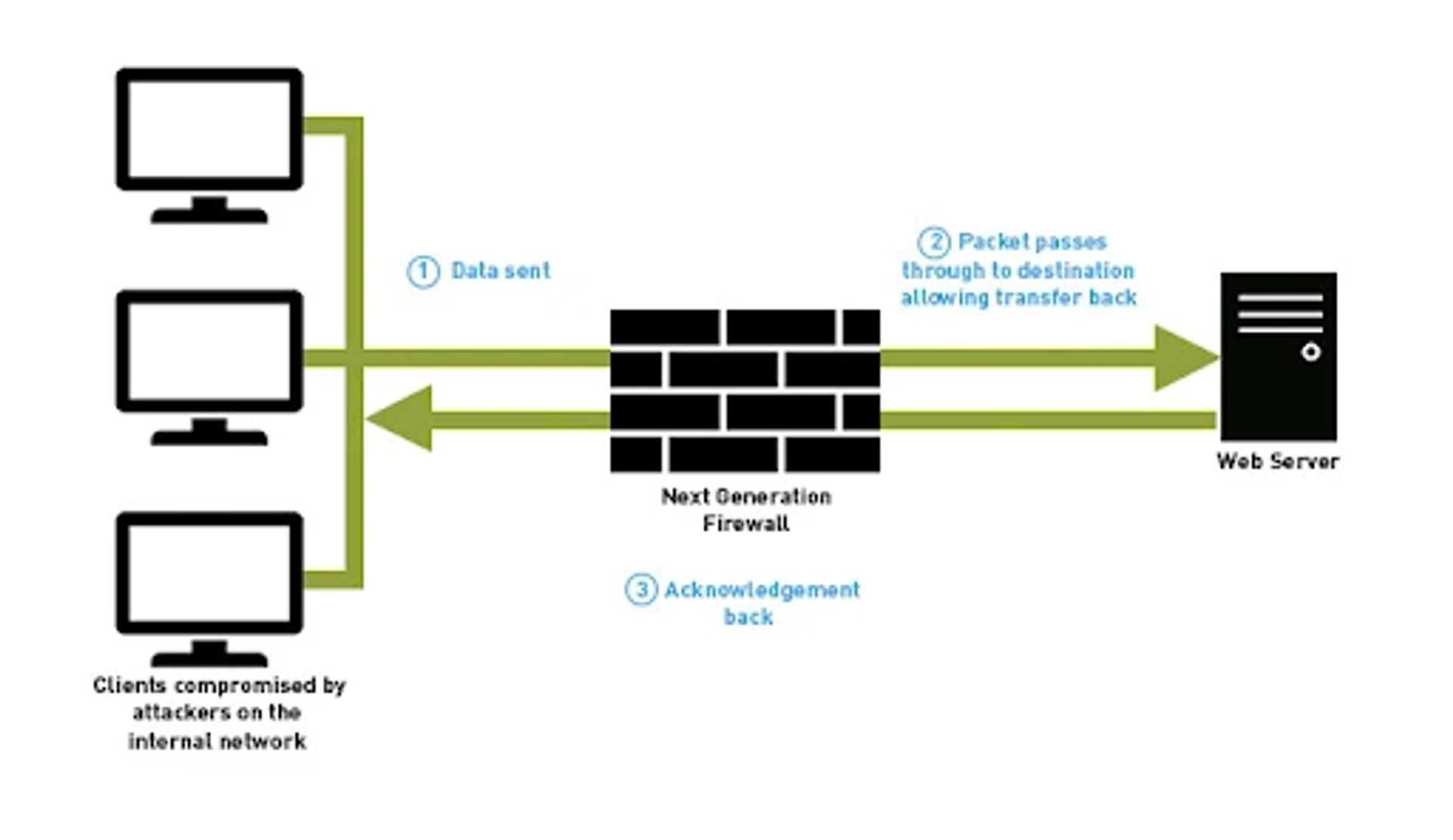
 Next-Generation Firewalls
Next-Generation Firewalls
Next-Generation Firewall (NGFW) is a deep-packet inspection (DPI) firewall with stateful inspection and other security systems such as malware filtering, antivirus, and IDS/IPS. Next-gen firewalls move beyond the protocol to bring intelligence from the outside of the firewall network. It adds application-level inspection and prevents intrusion.
What Is Network Firewall Used For?

Network Firewalls are used by both consumers and corporate professionals. Modern organizations use firewalls for security information and event management strategy. They even include various cybersecurity services other than the mentioned ones. The main reason to install Firewalls is to guard the organization against internal or external threats as it creates a segmentation between threats from the outside as well as inside.
In addition to protecting the organizations from threats, Firewalls also perform functions such as login and auditing. Some major uses of Network Firewalls include keeping track of events, constantly updating the rules, filtering traffic, and altering the user to intrusions.
Firewalls prove to be extremely useful when talking about always-on connections such as Digital Subscriber Line (DSL). The connections like DSL are in need of static IP addresses, so Firewalls are always preferred. Network Firewall Security is even used apace with antiviruses.
How Does Network Firewall Security Work?

Network Firewall Security ensures some kind of stoppage between external traffic and your private network or the network it is guarding. It puts a protective layer around your network which prevents several security threats such as remote logins, Marcos, spam, viruses, etc. It acts as a packet-scanning security device, where packet refers to pieces of information or simply data information. As we've mentioned, Network Firewall Security uses a series of predefined rules that become a base for filtering out malicious and benign activities. Network Firewalls use this packet to determine whether or not the given packet of information abides by the predefined rules.
The focal points of the predefined set of rules include:
- Source
- Content
- Destination
The representation of these focal points might differ depending on the levels of the network. When information is passed through the firewall network, it is reformatted or restructured to clarify its location to the protocol. Let's take a look at some advanced features of Network Firewall Security.
Features Of Network Firewall Security
By now, you all must have realized the importance of Network Firewall Security in a business. Its ability to choke and block the external traffic or network from disturbing your private network is commendable.
In addition to this, Network Firewall Security has other features as well, that we're going to discuss in this section.
 Integrated Security
Integrated Security
What's more complex than anything else is a network's security and safety. Organizations work with several known and unknown networks every day, which makes it a complete necessity to verify the authentication of the sources used. In this modern era, cyber crimes are becoming more frequent with advanced threats.
So, organizations adopt Network Firewall Security which helps alleviate complex security and safety processes. Integrated Unified Security Management (USM) easily manages the security of an organization and allows the security teams to prevent or minimize the cyber risk.
 Cyber Risk Prevention
Cyber Risk Prevention
Cyber threats are becoming more frequent with time. The longer cyber threats are left untreated, the more damage companies are bound to pay. Ransomware can slow down the system, decrease productivity, and make you lose profits.
Thus, organizations need threat and cyber risk prevention, which can be assured with Network Firewall Security. Firewalls detect external threats and block them from getting encountered with your network. Firewalls come with integrated threat prevention functionality, anti-phishing, anti-malware, anti-bot, and a high-quality threat intelligence feed. All the factors are essential components of an organization's network security.
 Hybrid Cloud Base
Hybrid Cloud Base
Today, organizations use cloud-based platforms in their businesses. Many of them use the hybrid cloud as it ensures better security, productivity, operations, and growth. With the hybrid cloud, it is easy to take care of different security conditions of both public and private networks.
That's why it is important to adopt Firewalls with Hybrid Cloud as a base, which will make it easy to deploy and enable organizations' security from one console.
 Scalability
Scalability
The sole reason for organizations shifting from conventional business to cloud-based business is the increased scalability and flexibility. Everyone wants to extract the benefits of cloud platforms. Network Firewall Security is an appropriate option when it comes to business efficiency, scalability, and flexibility.
 Application Identification
Application Identification
The organizations keep evolving by deploying new applications that are useful for the corporate networks. An advantage of a Firewall is that it identifies several applications generating one or another kind of traffic. It can even identify employees based on their roles assigned. Network Firewall Security also supports policy creation and allows employees to use varying sets of applications.
How To Install Network Firewall Security?

The installation of any application can be a real challenge if you're new and don't a thing about the same. But, you should breathe the worries away, as we've tried and broken down the steps to download and install the Firewalls on your systems. Below are the easy 4 steps to install, configure, and test a network:
Step 1: Secure access to the firewall network
We're sure you don't want any third party interfering with your firewall networks and settings. So, we advise you to give the administrator access handle to only those who are trusted and reliable. When they enter their login credentials, secure them with extremely strong passwords.
If the number of people using the Firewall exceeds, you can create multiple accounts in their names. Because using the same account or sharing accounts won't be a good option in terms of security and accountability.
Step 2: Architecture Firewall And IP Addresses
The best protection happens when you know your system inside out, so you should try and get to know about your networks. Once you set up the access controls, you're free to create multiple zones. Plan out a structured way to keep attackers away as an easy way for you might be a very easy way for the cyber criminals to attack.
You must make sure that Network Address Translation (NAT) is configured so that it allows external devices to communicate when necessary. Once you're done creating your structured zone and correspondence IP address scheme, you're set to create your firewalls space.
Step 3: Firewall Configuration
Firewall Configuration is the most important step that lets you configure and set the rules through which you can control the traffic of your network. Firewall Configuration lets you filter the data per various rules set to monitor traffic going into different network zones. If you want to restrict every traffic other than the allowed one, you can use the “Deny All” option.
You need to make sure that the Firewall's ability to control next-generation level flows is on point. As you pay for Network Firewall's advanced features, don't forget to verify them.
Step 4: Firewall Testing
The last step is to test your Firewalls properly to check if it is choking or blocking the unnecessary traffic from entering your private network. Penetration testing can be implemented to check and validate the strength of your Network Firewall Security.
What Are The Components Of A Good Firewall System?
Component-based applications are known to provide quality, speed, and easy deployment. You can judge how good an application is by looking at its components. Similarly, a series of components contribute to the goodness of Network Firewall Security. Below, we'll broadly discuss the building blocks of a good firewall system:
 Perimeter Router
Perimeter Router
A Perimeter Router provides links to the public or communal networking systems, such as the internet or such exclusive platforms. It follows an appropriate protocol or process to route the data packets. Perimeter Router even offers various address translations and information or data filtration.
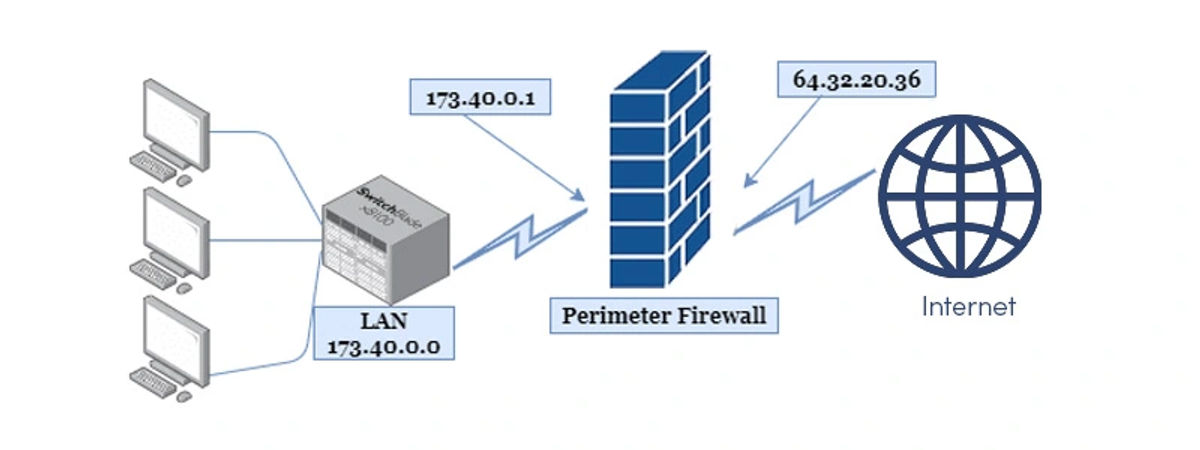
 Firewalls
Firewalls
As mentioned above, a Firewall is a device that monitors the traffic and allows only authorized traffic to encounter your private networks. It is a guarding device working against cyber criminals or attackers. As the role of a Firewall is to prevent or minimize the external threats, they're placed near the router but because not every threat can be an external one, so to prevent the internal ones Firewall is present in the internal networks.
 Virtual Private Network (VPN)
Virtual Private Network (VPN)
A Virtual Private Network or commonly known as VPN is a feature establishing a secured connection between two networks or devices. It includes encryption, authentication, and reliability assurance. With VPN, remote access to the network has become secure, so it connects two WAN networks without them being connected physically.
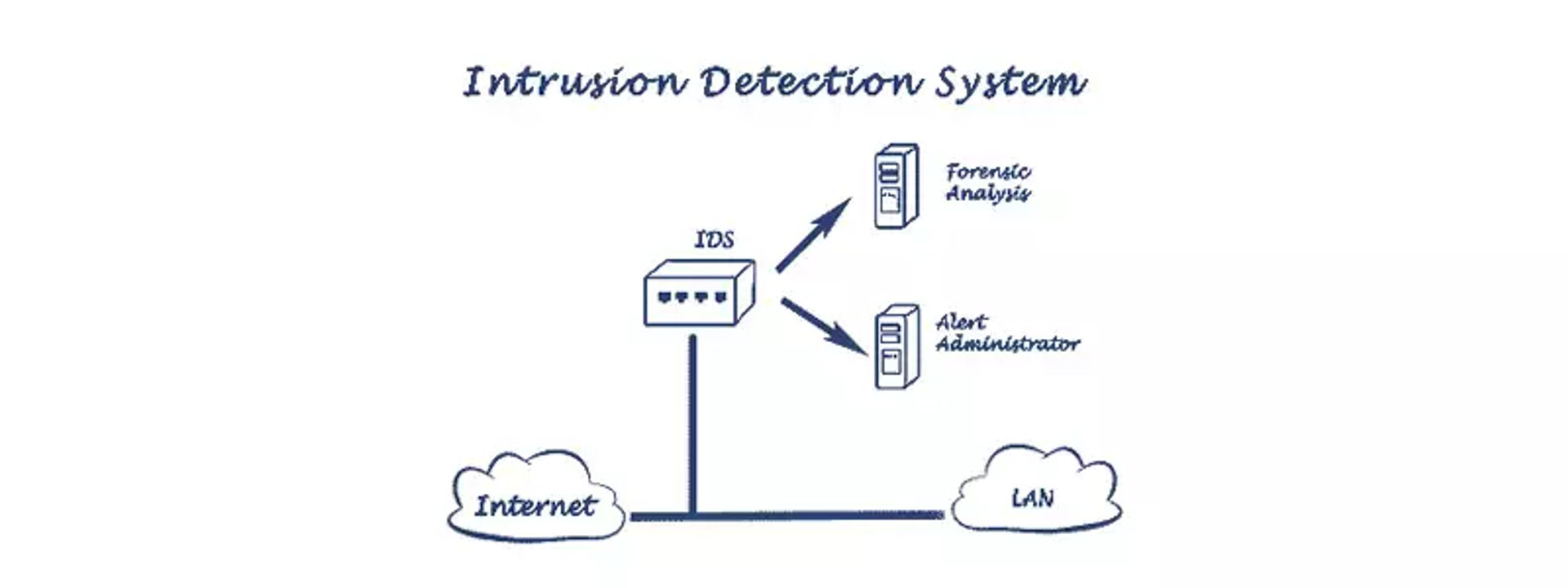
 Intrusion Detection System (IDS)
Intrusion Detection System (IDS)
An Intrusion Detection System, commonly known as IDS, detects and resolves external or unauthorized threats. Cybercriminals can execute a DoS attack, an attack from the backside, or any attack using an authorized or unknown network. So, IDS is an important feature as it smartly deals with such malicious activities.
Pricing/Cost Of Network Firewall Security
The pricing of Network Firewall Security depends on various factors such as the organization's size, type of firewalls, etc. If you're going for a Hardware Firewall for a small-medium business, it can range anywhere between $700-$1,000. If your business operates with a larger number of people, say 100, then the amount can go up to $1,500 to $4,000.
Other than the organization, there are some more factors determining the price of the Network Firewall Security:
- Make, Model, Characteristics, Capacity, Performance, and redundancy
- The cost of the support subscriptions and the current security services
- Maintenance of the Firewall includes configuration, monitoring, and integration
The basic cost range of a Firewall is determined by the users, locations, workload, bandwidth, etc. Normally, you buy a firewall license for 1 to 3 years and renew the license when the term is over. So, the pricing for that license ranges between 2 to 3 times for Hardware Firewalls. So, if a small Firewall is around $700, it can go up to $1,500 for 3 years of the term.
What Makes Network Firewall A Good Security Device?
A Network Firewall has every feature that a security device should own. It comes fully prepared for every type of threat.
If we talk about Firewall features' contributions, it will be broken down into 3 major things:
 Monitoring Traffic
Monitoring Traffic
The best feature of a Network Firewall Security is its monitoring abilities. A firewall always monitors the traffic and only lets authorized traffic enter your network. It does not allow unauthorized or unknown traffic to enter your private network. This feature is the best to keep your network inaccessible to unknown sources.
 Preventing Threats or Attacks
Preventing Threats or Attacks
A Firewall is known for guarding your network against malicious activities, external or internal threats, and several attacks. It creates a security boundary by filtering out unnecessary traffic from your network. With Network Firewall Security, you don't have to worry about your network's security and privacy.
 Data Security
Data Security
Firewalls filter out the traffic and do not allow any external traffic to threaten your network settings, so Firewalls are a great choice to secure your organizational data. It does not allow alien information to enter the network, so it will keep your sets of data safe and secure. If you want to secure your data organizational data with every detail as it is, you should go for Network Firewall Security.
Limitations Of Network Firewall Security

A Network Firewall Security is an exceptional security device with multiple features and advantages. However, every coin has two sides. If a firewall has various benefits, it also has some disadvantages that we'll discuss further in this section.
 Cost
Cost
Using Network Firewalls is a good option until you go through its pricing processes. Usually, Hardware Firewalls are more expensive than Software Firewalls. Hardware Firewalls require high maintenance and proper installation, which can become a little over-budget. Hardware Firewall requires IT experts as the configurations involved are complex.
 Restricted Use
Restricted Use
We all know that Network Firewall is used to choke the unknown traffic from entering your networks. While SMBs might find it an advantage, businesses with larger bases may face difficulty. The strict Firewall policies do not allow employees to perform certain tasks at times, because of which the overall organization's productivity is hampered. Firewalls use backdoor exploits, but they can damage the security of your network as the backdoor exploits do not check the data thoroughly.
 Performance
Performance
Network Firewalls, especially Software Firewalls, can decline the overall performance of your systems. The RAM and processing power determine the performance of your computer and when a firewall is constantly running in the background of your system, it declines the performance of your system.
 Malware Attacks
Malware Attacks
Although Network Firewall is known for blocking all sorts of attacks, it becomes defense-less in case of Malware attacks. Malware attacks enter your network as trusted data and affect the system to its worst. So, it is advisable to still install anti-malware even after getting Network Firewall Security.
 Complexities
Complexities
The SMBs can well manage the operations of Firewalls as they don't require much to set it up. However, large-scale organizations find it difficult to manage Firewalls set up as there is a separate section to operate firewalls. This staff ensures data security by handling Firewalls.
Best 5 Network Firewall Security Software (Paid/Free)
Network Firewall Security is an integral part of an organization's network security. There is a wide variety of options when talking about Firewalls. We know you want to choose the best security device for your network, so here we've prepared a list of the best Network Firewall Security Software that you can choose for your organization:
SolarWinds Security Event Management
SolarWinds provides security and safety to your private network with a security event manager. The features attached to SolarWinds provide strength and reliability to your network. It continuously monitors the network and detects malicious activities at the earliest, by using event correlation. SolarWinds even uses policy checks to detect any threat.
Price: The pricing of SolarWinds Security Event Management starts at $4,805 with a free trial for the first 30 days.
CrowdStrike Falcon Firewall Management
CrowdStrike Falcon is a complete security and safety suite that provides various features such as protection against viruses (anti-virus), firewall security, and more under the brand name Falcon. With CrowdStrike's network security settings, each device gets a separate defense or security system. However, your system will still have a centralized control system.
Price: The pricing of CrowdStrike Falcon depends on the type of subscription you're taking. It has three categories: Falcon Pro at $8.99/month, Falcon Enterprise at $15.99/month, and Falcon Elite. You can get the pricing details for Falcon Elite from the official website of CrowdStrike Falcon Firewall Management.
ManageEngine Firewall Manager
If you're a small or medium-scale organization, private or government IT enterprise, then ManageEngine Firewall Manager is the solution for you. It provides structured firewall management and a Firewall Analyzer. ManageEngine strengthens your network settings and does not allow any external traffic to enter your network. This tool provides real-time visibility and commendable monitoring skills.
Price: The pricing of ManageEngine Firewall Manager starts at $395 with a free trial for the first 30 days.
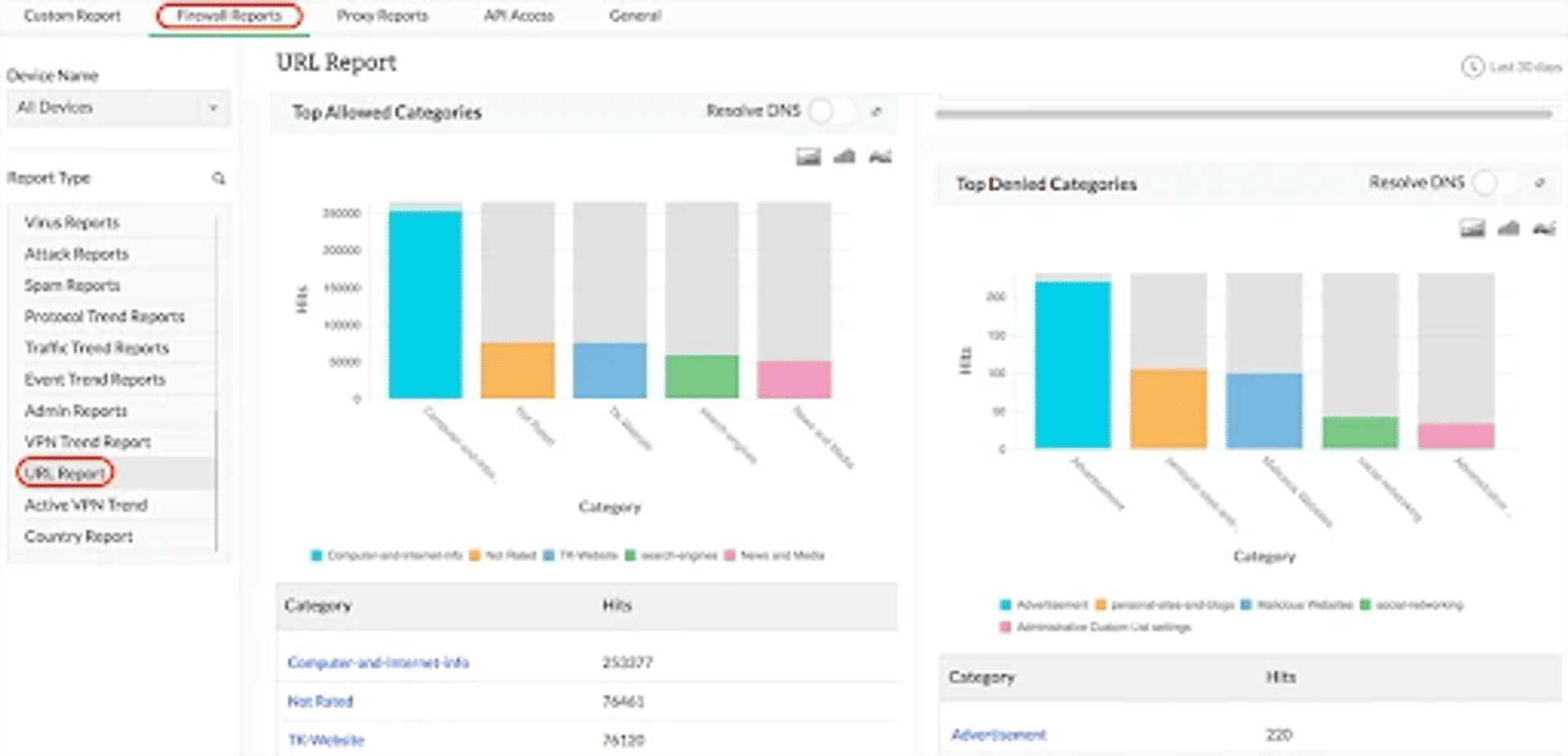
Zscaler Cloud Firewall
Zscaler Cloud Firewall is a cloud-based firewall security device that detects HTTP/HTTPS traffic. It works through the user routing traffic and has an SSL inspection that helps catch the cybercriminals who use encrypted traffic to enter your network. Zscaler has multi-site, remote device coverage, SD-WAN, and bandwidth management. If you're using Zscaler, you can monitor your security activities in real-time and control what enters your traffic through Granular Firewall Policies.
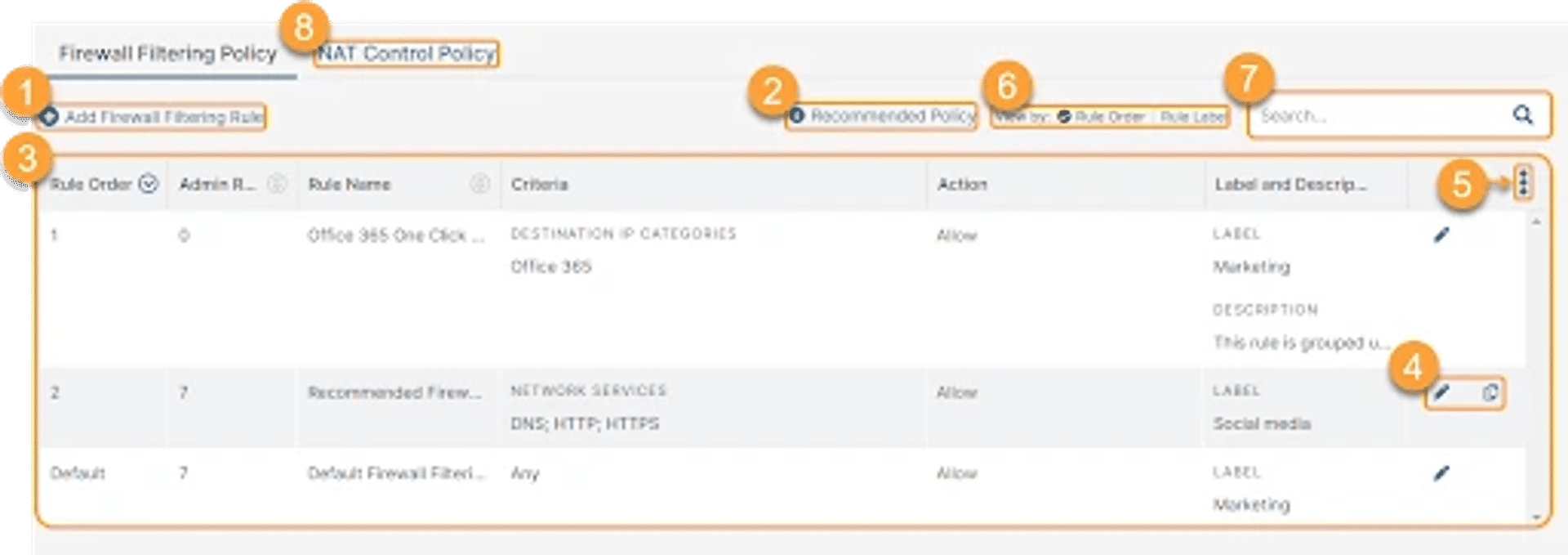
System Mechanic Ultimate Defense
System Mechanic Ultimate Defense provides a complete security and safety suite. It safeguards your performance features and manages your passwords and credit cards well. System Mechanic has the power to choke, block, or even remove malware attacks. It has a malware killer that extracts the virtual infections out of your system.
Price: If you use System Mechanic Ultimate Defense, you'll get a flat 60% off at just $31.98. If you're a new customer, you can use the coupon code “workfromhome” to get heavy discounts.
Alternatives To Network Firewalls 2022
We would like to take a moment to address how window firewalls are not very friendly when it comes to navigating and other uses. Windows-based firewalls can well protect your systems (computers, laptops, etc.) for network security optimization, it is necessary to attach a third-party firewall.
The monitoring feature of windows-based firewalls is quite weak and fails at detecting malicious activities. But, we don't want you to stress over something as basic as Firewall.
So, here we'll discuss the best 5 alternatives to Network Security Firewall:
 GlassWire
GlassWire
GlassWire comes with a package full of advantages and features. It does not only take care of your system's security but also focuses on intrusion detection. Its interface is easily understandable with finely structured functions. You get a series of features like data tracking, visual network monitoring, network checks, lockdown mode, etc. It is a stamp for providing proactive protection against threats.
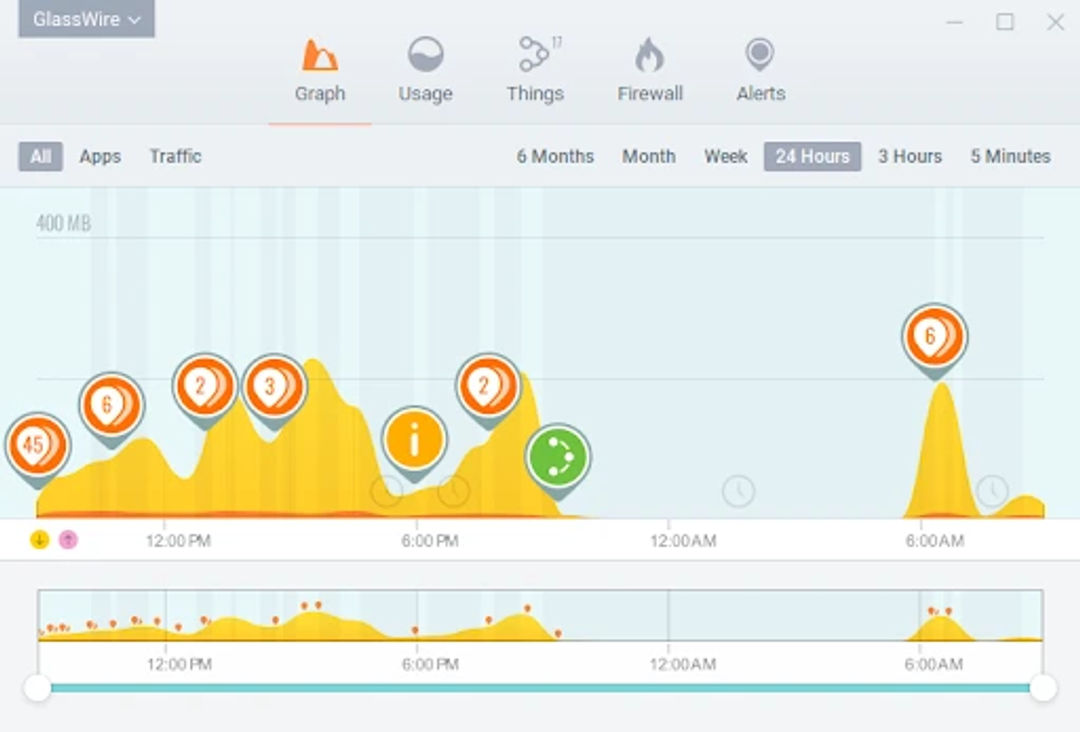
Visit https://www.glasswire.com/ to know more about GlassWire.
 TinyWall
TinyWall
TinyWall is a free firewall device that protects your network from external or internal threats. It is a lightened device, but its power is commendable. TinyWall has some of the highest security features, so we recommend this to everyone. Once you install TinyWall, you'll never experience annoying virtual lags such as pop-ups. TinyWall has an application scanner that scans your computer for programs that are later added to the safelist. With TinyWall, you can even choose a file, service, or any process.

Visit https://tinywall.pados.hu/ for more information about TinyWall.
 Comodo Firewall
Comodo Firewall
Comodo Firewall is a free network security device that is a chromium-based firewall. This tool has a series of advanced features like a Virtual Kiosk, ad blocker, etc. You can easily add programs to block them if you're using Comodo Firewall. It provides a shield to your system and does not let external and internal threats affect it. Besides the security feature, Comodo also has anti-malware and anti-virus features.
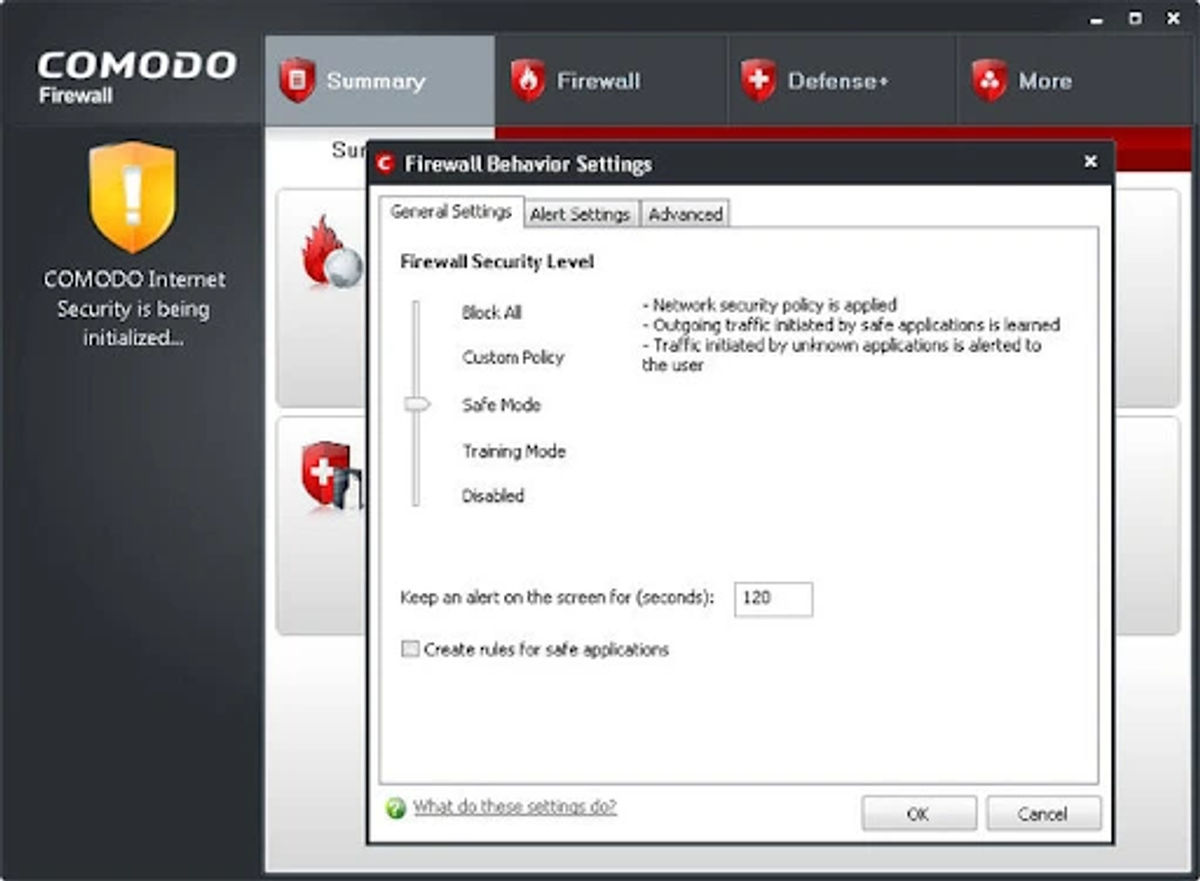
Visit- https://personalfirewall.comodo.com/ to know more about Comodo Firewall.
 Norton Smart Firewall
Norton Smart Firewall
Norton Smart Firewall, a component of Norton Internet Security Solution and Norton antiVirus, is also famed as Smart Firewall. Norton has a database of programs that are used for enhancing network security. It has a variety of advanced features like blocking the source of phishing, protection against cyber-attacks, monitoring, etc. It comes with an advanced IDS with many technologies. These advanced technologies help Norton detect and choke all the malicious activities.
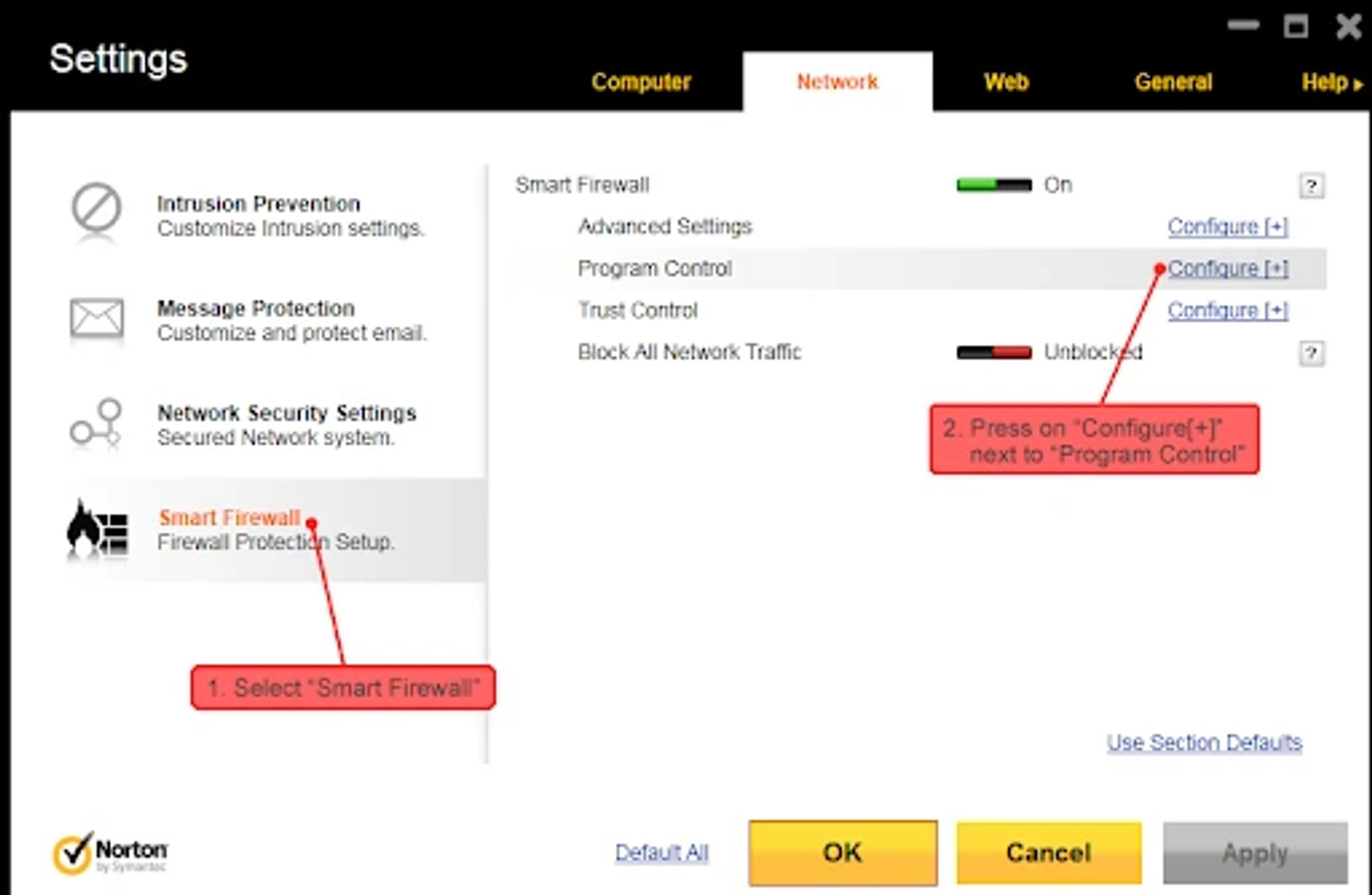
Visit- https://in.norton.com/ to learn more about Norton Smart Firewall.
 ZoneAlarm
ZoneAlarm
ZoneAlarm is a firewall security device that keeps your network safe and secure. It is a free alternative to Network Firewall Security that has several advantages like SmartDefense Advisor. The pop-ups on your screen are blocked by SmartDefense Advisor. You're allowed to install AUTOLEARN or MAX security when you're using ZoneAlarm. It protects your network and works against cyber threats, viruses, phishing attacks, etc.
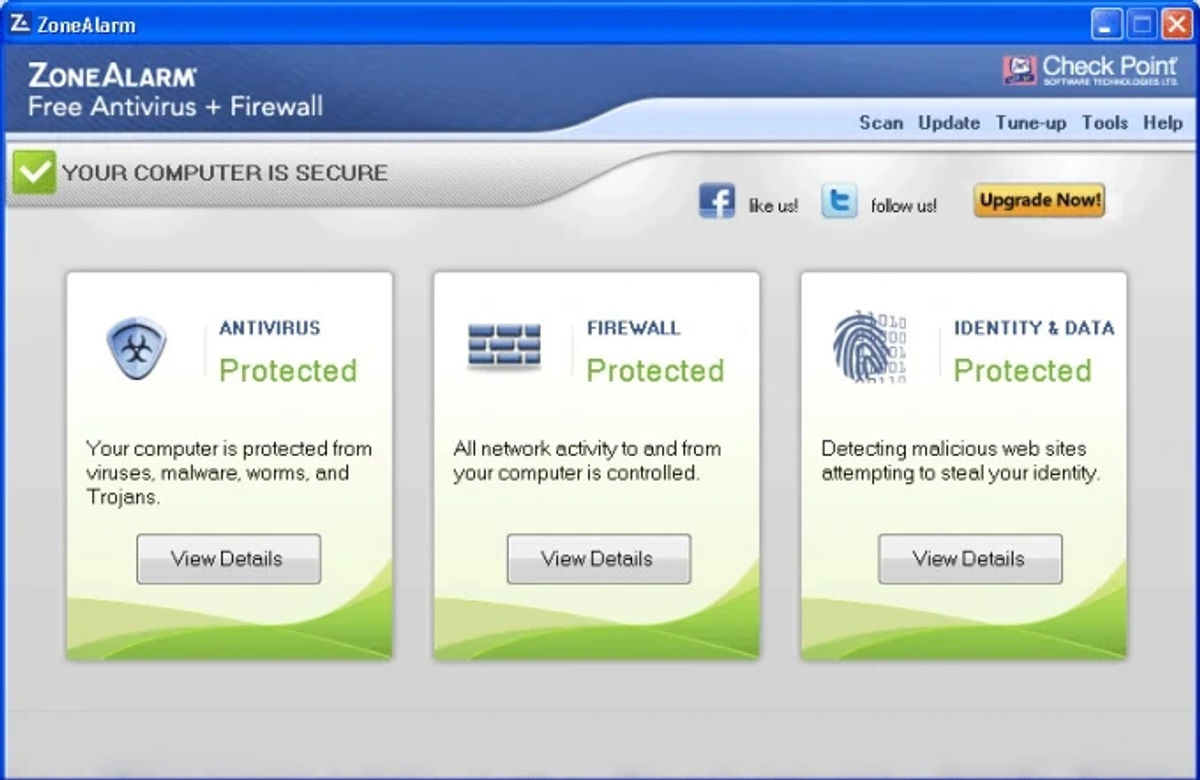
Visit https://www.zonealarm.com/ to learn more about ZoneAlarm.
Final Thoughts
The most important thing in a business is the protection and prevention of data from getting into the wrong hands. Once the organizational data gets leaked, it can lead to several business losses. That's why businessmen prefer locking their network with safety and security. Network Firewall Security, also known as Firewalls, in this case, is a helping hand. By now, you all must have understood the importance of providing your network with safety walls. So, the firewalls are those safety walls. When you entrust your network with firewalls, you create a boundary between external-internal threats and your system. We hope, with this blog you'll be able to find a suitable firewall for your network and protect it from cyberattacks.
If you liked our blog and don't want to miss out on similar content, do not forget to visit our official website as many such informative tech blogs are waiting for you. For any queries, please contact our support team whenever you want. Thank You!
Visit https://www.zonealarm.com/ to learn more about ZoneAlarm.
Trusted Partners Play a Vital Role in Ensuring a Seamless Hosting Experience.
These carefully selected partners contribute their expertise in technology, infrastructure and support solutions, enhancing reliability and performance. Through this collaboration, Sagenext delivers a dependable and efficient hosting environment, allowing users to work without disruptions and enjoy optimal stability and security.
























Sagenext has consistently garnered distinguished recognition for its exceptional hosting services, characterized by a resolute dedication to innovation and customer delight. This unwavering commitment to excellence has been demonstrably acknowledged through the receipt of numerous prestigious awards and accolades, solidifying Sagenext's position as an industry leader.
 Great Uptime by HostAdvice
Great Uptime by HostAdvice Great User Experience by Finances Online
Great User Experience by Finances Online Rising Star Award by Compare Camp
Rising Star Award by Compare Camp Top 10 Cloud Hosting Host Advice
Top 10 Cloud Hosting Host Advice