Components and 5 Core Functions of Cybersecurity Framework
Table of Content:
Almost every one of us may have encountered the term “Cybersecurity Framework” and other similar terms like this, at some time or the other. But, if you are a business owner who is serious about their business, stop for a moment, please! And ask yourself now—do you know what this is and how it works, and why it is so important for you?
Don’t worry even if your answer is NO. At the end of this blog, you will have answers to each of your questions related to the Cybersecurity Framework with its five core functions, and security measures recommended by the NIST.
What is Cybersecurity Framework
Cybersecurity Framework, in layman’s terms, is a set of global standards, guidelines, or security practices through which an organization can combat any organizational security threat or risk in the digital world. It provides a structured method and enforces security measures to protect organizational digital assets..
Such guidelines are published and updated by the National Institute of Standard and Technology (NIST), a US government entity responsible for protecting small businesses from malicious activities like ransomware or malware attacks. It provides the required resources and support to help businesses update their IT procedures.
How Does It Work
As the framework is not industry-specific or country-specific, it offers a common taxonomy and mechanism for all types of organizations throughout the world. It is technologically neutral, which means the same kind of regulatory principles are applied everywhere no matter what type of technology an organization uses. And the best part is that it is voluntary, not obligatory.
This does not replace an organization’s existing cybersecurity programs or risk management processes, rather complements the existing ones. While aligning with the core industry practices, an organization can leverage the Framework to investigate opportunities, and can even introduce a robust security system to further strengthen their IT procedures..
A survey conducted in 2016 acknowledges that around 70% of industry leaders experience the Framework as both easy to accommodate and rewarding. It has considerably helped them strengthen their security posture to withstand almost any type of security threat.
Why is Cybersecurity Framework So Important
Another recent survey done by a global technology company, Insight, reveals that more than 70 % of business executives do not feel confident about handling unforeseen cyber-attack.
For the same reason, all our internet-run devices as well as our personal and business data have become heavily exposed to cyber-attacks growing rampant in the digital world. We can fall easy prey to cybercriminals anytime, anywhere.
And this is where the Cybersecurity Framework seems to be our best friend. In the digital world, the Cybersecurity Framework is a complete system or structure that underpins our digital security system or concept. A framework is, in fact, a way of organizing information and related tasks to withstand any possible threats.
Now is the time to discuss the 3 components of the Cybersecurity Framework which are the Framework Core, the Framework Implementation Tiers, and the Framework Profiles.
Components of Cybersecurity Framework
Components of Cybersecurity are explained in brief below:
1. The Framework Core
The National Institute of Standards and Technology (NIST) defines the Framework Core as a set of cybersecurity activities, desired outcomes, and applicable references that are common across all critical infrastructure sectors. It makes the communication of cybersecurity activities and outcomes possible across the organization, from the executive level to the operational level.
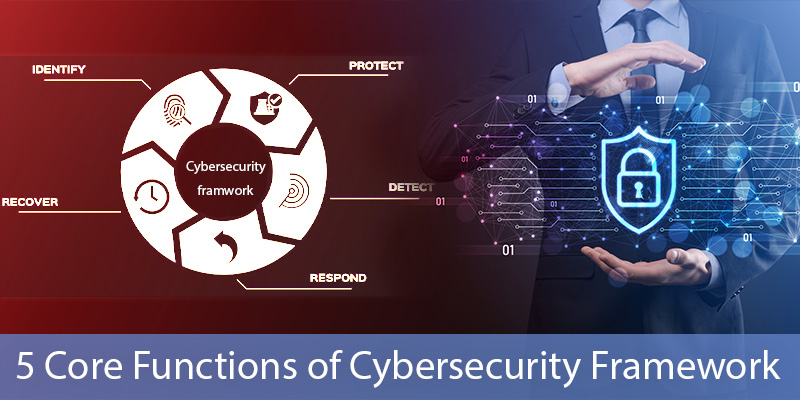
The Framework Core consists of 5 concurrent Functions:
Identify: Organizations should develop an understanding to manage several cyber threats.
Protect: An Organizations should develop security procedures to safeguard the data.
Detect: Organizations should detect suspicious activities within a network.
Respond: Organizations should take action against unethical cyber practices on the organization’s behalf.
Recover: Organizations should maintain plans for the convenient recovery of lost data.
2. The Framework Profiles
As laid down by the NIST in the Cybersecurity Framework document, the Framework Profile is the alignment of the Functions, Categories, and Subcategories to the business requirements, risk tolerance, and resources available to the organization.
A Profile makes organizations capable of creating avital blueprint to mitigate any type of cybersecurity risk that is well-aligned with the ever-changing organizational goals and requirements. It takes into account their risk management goals as per their individual organizational needs.
3. The Framework Implementation Tiers
Just as the Profiles and the Framework Core, the Framework Implementation Tiers are designed to perform specific tasks. They help an organization examine the existing cybersecurity risk management systems and practices and plan to further strengthen its security posture.
The Implementation Tiers part describes the extent to which organizations’ cybersecurity risk management practices demonstrate the characteristics laid down in the Framework. The Tiers range from Tier 1 (Partial) to Tier 4 (Adaptive)
Now that we have got a clear understanding of these three components, we are in a very comfortable position to understand the NIST five Functions described below.
NIST 5 Functions of the Cybersecurity Framework
The Cybersecurity Framework is further divided into 5 high-level Functions, Identify, Protect, Detect, Respond, and Recover, all are focused because of their importance in maintaining holistic cybersecurity.. They act as a skeleton of the Cybersecurity Framework that all other elements are structured around.
This Framework is simple and easy to understand, and it works as a translation layer to facilitate secured communication between cross-functional teams. This helps organizations address all their cybersecurity risks and enable them to take efficient risk management decisions.
Now, let’s take a deeper look at how these Cybersecurity Functions perform.
1. Identify
It is the most fundamental of the Cybersecurity Framework functions. Under this Function, executing extensive background is necessary to safeguard the organization’s whole security system.
As the name suggests, this is all about the identification of organizational resources, assets, systems, data, and other capabilities in the business context, as well as the respective cybersecurity risks. The activities in the Identify Function are crucial for the effective use of the Framework to manage all possible cybersecurity risks.
Examples that fall under the Identify Function are:
- Asset Management
- Risk Assessment
- Risk Management Strategy
- Business Environment
- Governance.
2. Protect
By following the Protect Function, an organization can implement and advance its security measures. It ensures the smooth delivery of hypercritical IT infrastructure services.
To comply with this Function, it’s essential for organizations that they have proper control over access to all their physical and digital assets. They must have a system of providing security awareness education and training to their staff members. They need to put a well-established process in place to protect data, maintain a baseline of security in network configuration and operations, repair components of the security system in time, and deploy robust defensive technologies to ensure strong cyber resilience.
The Protect Function gives organizations the ability to curb the adverse effects of possible cyber-attacks.
3. Detect
The Detect Function helps organizations implement and develop the needful activities to quickly identify the occurrence of any cybersecurity breach in a timely fashion.
To comply with this Function, organizations need to adopt a perpetual monitoring system to detect operational continuity threats, if any. Organizations need to have clear visibility into their networks to envision any cybersecurity events.
Examples of outcome Categories that fall under Detect Function are:
- Detection Processes
- Continuous Security Monitoring processes
- Anomalies
- Events
4. Respond
The Respond Function enables organizations to implement and develop appropriate activities to take the required actions against the cybersecurity breaches that are already detected.
To comply with this Function, an organization needs to have an efficient response plan to counter the security risk if found. Additionally, they must have all the appropriate security measures to respond accordingly and quickly.
Examples of outcome Categories that come under Respond Function are:
- Analysis
- Communication
- Response Planning
- Mitigation
- Improvements
5. Recover
The Recover Function helps organizations implement and develop effective security measures to safeguard their services and capabilities against the impact caused by any cybersecurity breaches. To comply with this Function, organizations must have an efficient recovery plan.
Examples of the outcome Categories falling under Recover Function include:
- Recovery Planning
- Communications
- Improvements
Conclusion
To sum up, NIST Cybersecurity is widely accepted as the gold standard for establishing a Cybersecurity Program, and implementing the same can certainly help your organization become more focused on managing and protecting critical IT assets and resources. Many tools in the market can simplify compliance with this Framework.







