What are the Top 10 Emerging Cybersecurity Challenges?
The total dependency of the world on the Internet for even the most basic things has made data security the need of the hour. Now, if we look at the amount of sensitive information the Internet carries, from your home address to your credit card details, cybersecurity challenges becomes indispensable.
According to Check Point Research, global cyberattacks increased by 38% in 2022, compared to 2021. This increase was driven by a number of factors, including the rise of remote work, the increasing use of cloud computing, and the growing sophistication of cybercriminals.
Likewise, in 2022, data breaches dominated the headlines. Companies from Twitter to Microsoft to American Airlines were the victims of data breaches as cybercriminals continued to wreak havoc in enterprises, disrupting business continuity and hindering business success. Data breaches like these impacted 422.1 million people last year, a 41.5% increase over 2021, according to the Identity Theft Resource Center (ITRC).
What is Cybersecurity?
Cybersecurity is the practice of protecting systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. Cybersecurity challenges are the threats and vulnerabilities that organizations face in protecting their information and systems from these threats.
Top 10 Emerging Cybersecurity Challenges Industry is Facing in 2024-26
1. Ransomware Attacks
Ransomware is one of the biggest cyber security challenges that concerns us in the digital world. In the year 2021- 2022, there were an unparalleled number of ransomware attacks, and this trend is still to continue in 2024.
As the word ransom suggests, it’s hacking into the user’s sensitive information and denying them access to it until a ransom amount is reimburse to the hackers. As depicted in the below image:
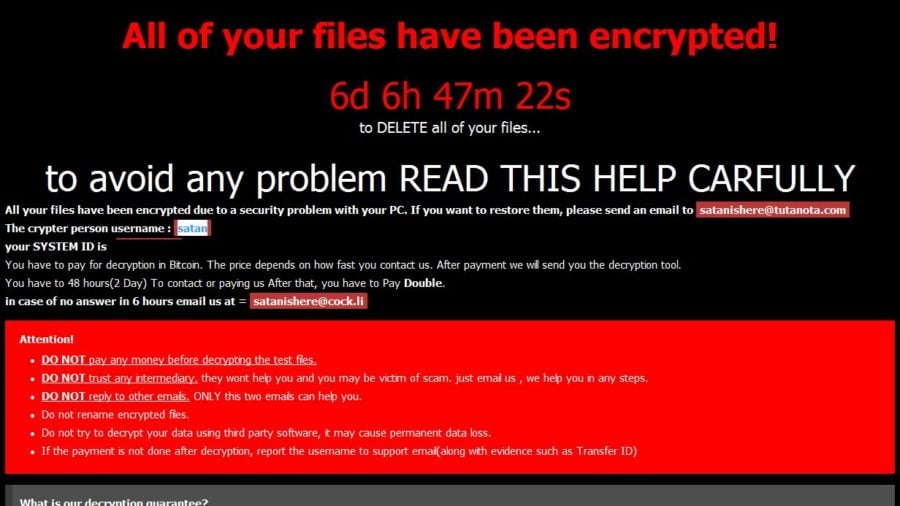
Now, businesses that need access to their data to run their daily operations suffer a lot from this breach, highlighting a serious emphasis that needs to be given by them on their data security strategies.
As per a study from ASTRA IT, 1.7 million ransomware attacks occur every day, with a ransomware attack occurring every 2 seconds. As much as $1.85 million was lost in the average ransomware assault. The WannaCry ransomware outbreak cost the National Health Service (NHS) an estimated $100 million.
Besides this, more and more attacks were reported after the pandemic since every information circulated was using the means of digitalization.
“Still, ransomware attacks are not new. Businesses, governments, and even individuals have been victims of ransomware attacks for over three decades now” – as explained in the detailed article of What is Ransomware? By Sagenext.
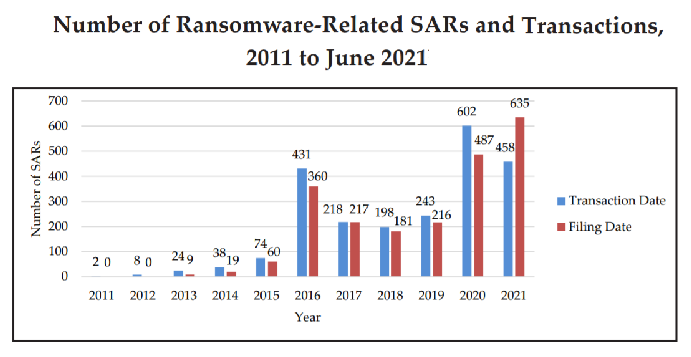
According to the Financial Trend Analysis report by Fincen (Financial Crime Enforcement Network), suspicious activity related to ransomware SARs in the first half of 2021 estimated $590 million exceeded the total reported for all of 2020 ($416 million).
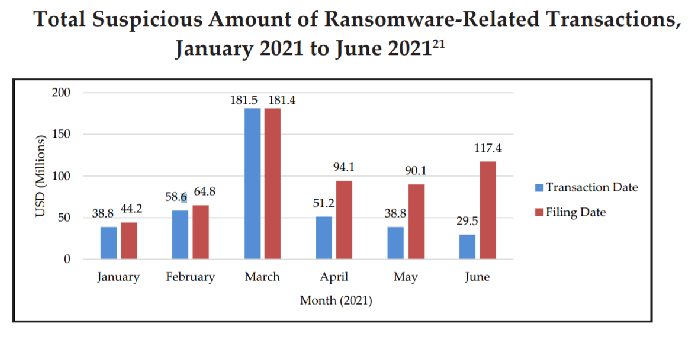
Doppel Paymer, Clop, Bit Paymer, Conti, DarkSide, and many more are the top cybersecurity ransomware variants that still remain active in the cyber world. So, a close watch out for ransomware attacks is a critical aspect for businesses.
2. IoT Attacks (Internet of Things)
The Internet of Things or IoT is the most vulnerable to data security threats. Every digital, mechanical, computing smart device that can transmit data over the internet network are termed as IoT such as; laptop and mobile phones.
In order to access your personal device that contains your sensitive information, hackers use devices that surround you, such as wearable smartwatches, baby monitors, smart fridges, or smart lights.
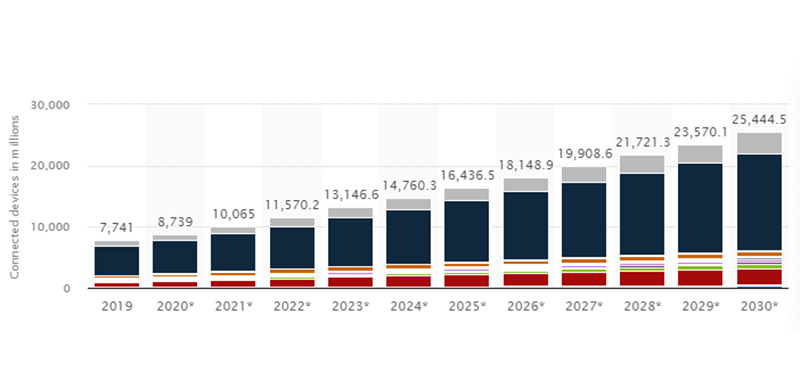
The IoT sector is the primary target for hackers looking to access users’ sensitive data. In 2024, the number of connected devices is predicted to increase to more than 14.4 billion. IoT Analytics claims that by 2025, there will be more than 27 billion gadgets online simultaneously. Around 12 billion devices were online by 2022, and this figure will rise to 25 billion by the end of 2030, as per the data.
As a result it will open a wide space for the hackers to attack the compromised data security and use them for malicious purposes.
3. Cloud Attacks
Cloud computing is the modern era of new technology that revolutionized the physical world of data storage. Businesses from large to small now utilize cloud services for storing their user-sensitive information.
On the one hand, where adoption of it has reduced the cost and increased efficiency, it has also opened possibilities for data security breaches.
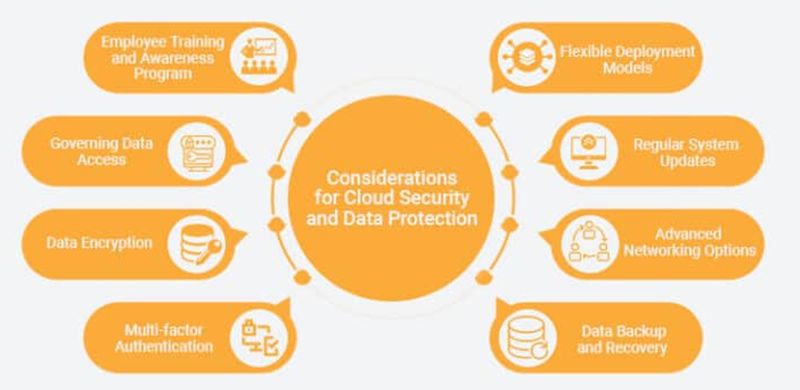
The main reason for compromised data security is the lack of encryption, authentication, and improper configuration of the cloud setups. So, they need to maintain many considerations for cloud security and data protection, to keep the sensitive information intact.
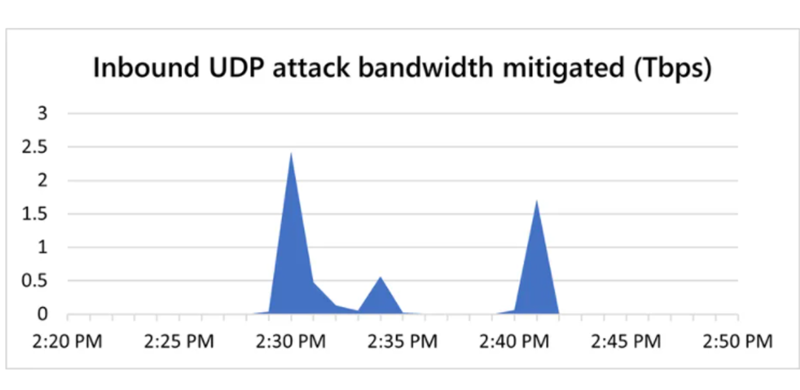
A recent case of Microsoft 2021 had made headlines, where the enterprise suffered a denial of service attack that made it almost impossible to access their cloud data service. In their official statement, Microsoft stated that the attack lasted for 10 mins and they were able to dodge the attack. “Business as usual for Azure customers despite 2.4 Tbps DDoS attack” – said Amir Dahan ( Senior Program Manager)
Still, it gives a fact check on how even the leading companies like Microsoft that practices strict cybersecurity protocols face cloud attack. In light of this, even small firms and professionals who use cloud setups are not-at-all exempted from these attacks.
4. Phishing Attacks
A phishing attack is a type of social engineering attack that targets users’ login details and credit card information. In contrast to ransomware, here the information benefits the hacker. Gmail is a Google service that is used across the board for almost everything from business to personal purposes.
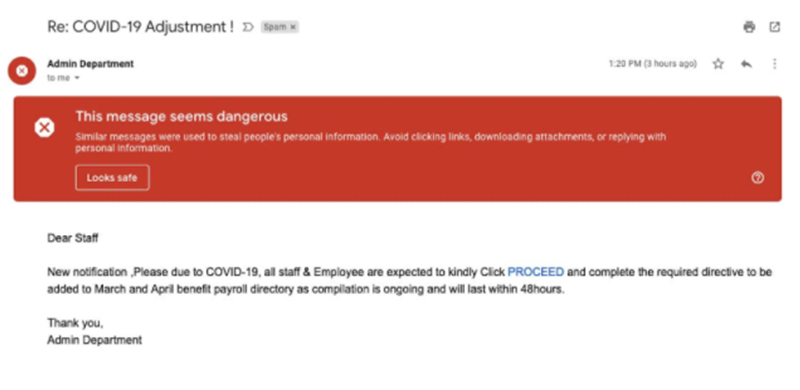
Now, whenever you open your mail account, you might come across a spam folder that consists of emails that the platform recognizes as a threat to your data security. These spam emails consist of thousands of phishing attacks that your mailing partner recognizes and warns you about the potential cyber threat that it carries. Yet, some of the communications still make it to your inbox where you might fall into a trap.
Officially, Google released a statement of how it blocks more than 100 million phishing emails on an everyday basis. It further emphasized how most of the communications were trying to impersonate government officials, authorities, agencies, or websites in order to sound more reliable to mail recipients.
5. Cryptocurrency and Blockchain Attacks
Digital currency or wallets are one of the prime targets of hackers and have posed many cybersecurity challenges for data security. Many blockchain attack variants such as Eclipse, Poly, DDOS, and Sybil made the headlines possessing a great vulnerability to the digital wallets. This is the main reason why blockchain technology is aiming to improve its cloud security with effective measures.
BBC reported in December 2021 that the BitMart exchange lost $150 million due to hackers that it became almost impossible for them to recover the investors amount. Furthermore, 177 unique convertible currencies digital wallet addresses were used for ransomware attacks as reported by the Fincen report. This in turn poses a great cybersecurity challenge for the market regulators to safeguard their investors data from such threats.
Hence, more possible cryptocurrency and blockchain attacks are likely to occur at an alarming rate in forthcoming years.
6. Mobile Banking Malware
This initially appears to be a huge obstacle for anyone concerned about ATM skimming. Also, new methods are being developed that will allow thieves to access bank accounts via smartphones and tablets. Similar to its predecessor, mobile banking malware steals login information, credit card numbers, and other private user data by taking advantage of vulnerabilities in devices.
Cybercriminals can empty your bank account within 30 minutes if their tactic remains successful. As a result, this has become one of the riskiest problems that banks will encounter in the year 2024.
7. AI Attacks
In 2024, consumers and businesses are likely to use AI even more. This could be good or bad for cybersecurity. AI can be used in the day-to-day work of security teams to do things like support security operations center analysts, find and stop threats, and manage and find fraud.
In 2021, nearly 68% of study respondents said artificial intelligence (AI) could easily be used for impersonation and spear-phishing attacks against their companies. It also noted that AI can boost ransomware, posing a threat to IT security.
Threat actos can use AI nefariously. To enumerate, attackers can run malware on AI to test its efficacy, poison AI models with inaccurate data, and map legitimate enterprise AI use to improve the success of their attacks. AI-enabled attacks, such as deep fakes, are becoming increasingly realistic for social engineering attacks.
8. Insider Attacks
Although most of the company’s cybersecurity challenges come from the outside, there are times when the danger comes from within. Data that should be kept confidential may be leaked by employees, which competitors may use.
Every day, about 2,500 internal security holes are found in US businesses. Insider threats ensue every year to more than 34% of companies worldwide. 66% of organizations believe that attacks from the inside are more likely than attacks from the outside.
As a result it can bring significant losses for the company’s finances and reputation. Monitoring the data and traffic coming into and going out of the network is a viable solution for mitigating these threats to computer security. The risk of insider assaults can lessen by installing firewall devices that route data through a centralized server or limiting access to files depending on work duties.
9. Social Engineering Attack
Humans can be socially engineered to give personal information. Fraudsters use people’s natural curiosity or trust, and voice manipulation is an example of advanced social engineering. An individual’s voice (from a voicemail or social media post) influence phone friends and ask for a credit card or personal information.
As per ZD NET, over 700 social engineering attacks happen annually against an organization. Costing businesses an average of $130,000 due to lost revenue or destroyed data, social engineering attacks are a serious threat.
Types of Social Engineering Attacks:
- Baiting
- Scareware
- Pretexting
- Shere phishing
- Vishing
10. The Man in the Middle Attack
Man-in-the-Middle attacks occur when attackers intercept two-party traffic—examples of criminals interfering with public Wi-Fi and a person’s device. The lack of a secure Wi-Fi connection allows cyber attackers to examine a victim’s data without being caught.
- In 2016, the SSL Store reported that about 95% of HTTPS servers were vulnerable to MitM(Man in the Middle) attacks.
- 35% of exploits resulted in MitM(Man in the Middle) attacks, according to IBM. Unfortunately, only 10% of businesses use HTTP Strict Transport Security (HSTS) to protect themselves from MitM(Man in the Middle) attacks.
- A study found that 43% of businesses were negligent in mobile security, making them vulnerable to man-in-the-middle attacks.
How to Deal with the Cybersecurity Challenges of 2024
Here cyber security challenges of 2024 are complex and ever-changing. Here are some tips on how to deal with them:
- Have a strong security posture. This includes having up-to-date security software, strong passwords, and a layered security approach.
- Be aware of the latest threats. Cybercriminals are constantly developing new ways to attack, so it’s important to stay up-to-date on the latest threats.
- Educate your employees. Employees are often the weakest link in the security chain. Make sure they are aware of the latest threats and how to protect themselves.
- Have a plan in place. If you get attack, it’s important to have a plan in place to respond quickly and effectively.
Moreover, here are some additional tips that can help you deal with the cybersecurity challenges of 2024
- Use a password manager. A password manager can help you create and store strong, unique passwords for all of your online accounts.
- Be careful what you click on. Phishing emails and malicious websites are a common way for cybercriminals to gain access to your systems. Be careful what links you click on and what attachments you open.
- Keep your software up to date. Software updates often include security patches that can help protect you from known vulnerabilities.
- Use a firewall. A firewall can help protect your computer from unauthorized access.
- Back up your data regularly. If your computer is infected with malware or your data is stolen, having a backup can help you recover your data.
By following these tips, you can help protect yourself from the cyber security challenges of 2024
Conclusion
Defenders will still need to be attentive in 2024, as it will be a power-up version of 2022. Businesses can harden their networks against data security threats with the right strategies – however, existing approaches aren’t always sufficient.
Fortunately, there are ways by which you can still protect your data security. Just like how Google in this tutorial illustrates on how to protect your Gmail account from phishing and malware attacks.
To summarize, by presenting 10 major challenges of Cybersecurity, we hope to increase awareness about upcoming cybersecurity threats and emerging trends.